VolgaCTF Quals 2018 - Forbidden
The Task came with the description:
Our friend tried to send us all his BTCs, but MAC of the transaction was lost.
We need your help to compute MAC for this encrypted transaction.
Send it in format VolgaCTF{AuthTag_in_HEX}.
And the following Python code:
from cryptography.hazmat.backends import default_backend
from cryptography.hazmat.primitives.ciphers import (
Cipher, algorithms, modes
)
from secret import key
def encrypt(iv, key, plaintext, associated_data):
encryptor = Cipher(
algorithms.AES(key),
modes.GCM(iv),
backend=default_backend()
).encryptor()
encryptor.authenticate_additional_data(associated_data)
ciphertext = encryptor.update(plaintext) + encryptor.finalize()
return (ciphertext, encryptor.tag)
def decrypt(key, associated_data, iv, ciphertext, tag):
decryptor = Cipher(
algorithms.AES(key),
modes.GCM(iv, tag),
backend=default_backend()
).decryptor()
decryptor.authenticate_additional_data(associated_data)
return decryptor.update(ciphertext) + decryptor.finalize()
iv = "9313225df88406e555909c5aff5269aa".decode('hex')
key = key.decode('hex')
ciphertext1, tag1 = encrypt(iv, key, "From: John Doe\nTo: John Doe\nSend 100 BTC", "John Doe")
ciphertext2, tag2 = encrypt(iv, key, "From: VolgaCTF\nTo: VolgaCTF\nSend 0.1 BTC", "VolgaCTF")
ciphertext3, tag3 = encrypt(iv, key, "From: John Doe\nTo: VolgaCTF\nSend ALL BTC", "John Doe")
And the textfile:
(C1, T1) = (1761e540522379aab5ef05eabc98516fa47ae0c586026e9955fd551fe5b6ec37e636d9fd389285f3, 0674d6e42069a10f18375fc8876aa04d)
(C2, T2) = (1761e540522365aab1e644ed87bb516fa47ae0d9860667d852c6761fe5b6ec37e637c7fc389285f3, cf61b77c044a8fb1566352bd5dd2f69f)
C3 = 1761e540522379aab5ef05eabc98516fa47ae0d9860667d852c6761fe5b6ec37e646a581389285f3
The encrypt function does an authenticated encryption of a plaintext and associated data using AES in Galois/Counter Mode(GCM).
The function outputs a tuple containing the ciphertext and a GCM authentication tag. The authentication tag guarantees that the ciphertext and the associated data (which is not encrypted) have not been tampered with.
So the task here is to forge a valid tag under an unknown key for the plaintext P3: From: John Doe\nTo: VolgaCTF\nSend ALL BTC with the associated data A3: John Doe. We have two valid ciphertext/tag pairs and the ciphertext of P3 to do so.
The cryptography Python module uses the supplied IV as nonce in the Counter Mode AES. The code shows that the same IV/nonce was used for all encryptions!
This is of course a very bad idea, and - as it turns out - two ciphertext/tag tuples together with their associated data is enough to forge authentication tags. Note that all these values are public in real encryption systems using GCM.
The calculation of the authentication tag in GCM can be seen in this graph:
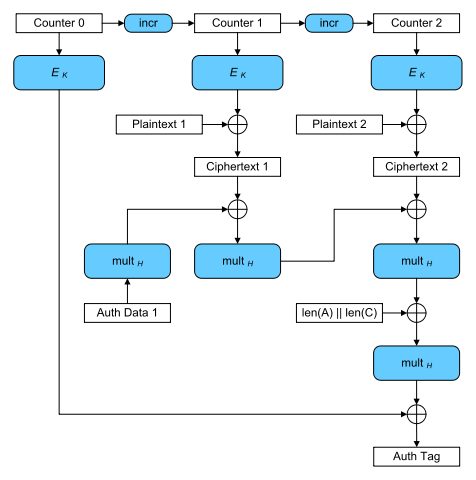
H is the hash key calculated by the encryption of a zero block under the encryption key . denotes the multiplication with H in the Galois Field .
To forge an authentication tag we employ the forbidden attack. The attack works if a nonce was illegally used multiple times (hence the name). It is described (a.o.) here.
So how does the attack work? The calculation of the authentication tag can also be viewed as a polynomial:
The authentication tag can then be calculated as .
The coefficients and , denote the associated data blocks and ciphertext blocks. denotes the length of the whole message and a nonce derived value. All of the coefficients are 128 bit long blocks used as binary polynomials in .
In our case, the polynomials used to create the known tags have the form:
With the same amount of associated data and ciphertext blocks as well as identical and . Evaluating these polynomials at H (the hash key) would give us the corresponding authentication tag . If we now deduct the tags from the polynomials:
we get polynomials that evaluate to 0 at H: , making the hash key H a root of both. Every coefficient in these polynomial is known except for , which is identical in both polynomials since the nonce was reused. So if we substract them from each other (note that adding and substracting is the same in ):
we get a polynomial with known coefficients and H as a root:
The roots of this polinomial are candidates for the hash key H. Since we work in adding the coefficients is the same as XORing their respective blocks.
Now we can calculate the missing by evaluating:
By putting all this together we can finally calculate the authentication tag for message 3. Since we know the ciphertext C3 as well aus the associated data A3 we just have to plug it in:
The final exploit gives us two possible flags, one per root:
$sage -python forb_expl.py
VolgaCTF{B084B54CB9D114C6912926F4EC42DBCF}
VolgaCTF{2AA1B52883378169C96072EA74BB41A1}
Turns out VolgaCTF{B084B54CB9D114C6912926F4EC42DBCF} was correct \o/.
Credits for this task actually go to my collegue chemmi who solved the task before me!